To recapitulate IPSec configuration by setting up Site-to-Site VPN with CLI and CCP with GNS3.
- Configuration with CLI
- Configuration with CCP (Wizard)
Topology
Suppose we have to interconnect 2 Branch LANs over insecure Internet:
- LAN1: 10.10.10.0/24
- LAN2: 172.16.1.0/24
 |
| LAN1 (R1 with 10.10.10.0/24) and LAN2 (R3 with 172.16.1.0/24) |
A) Configure R1
1) Setup IKE phase 1 (HAGLE)
crypto isakmp policy 12) Setup IKE phase 2 (IPsec transform)
hash md5
authentication pre-share
group 2
lifetime 10000
encr 3des
!
crypto isakmp key mys3cr3t address 2.2.2.2
crypto ipsec transform-set SCLabs-SET esp-aes 2563) Create ACL to match IPSec traffic will be encrypted
access-list 110 permit ip 10.10.10.0 0.0.0.255 172.16.0.0 0.0.255.2554) Create Crypto-map with sequence "10" and linked to outgoing traffic direction (exit interface)
crypto map SCLabs-MAP 10 ipsec-isakmp
description -=vpn to 2.2.2.2 =-
set peer 2.2.2.2
set transform-set SCLabs-SET
match address 110
!
interface GigabitEthernet2/0
ip address 1.1.1.1 255.255.255.0
crypto map SCLabs-MAP
!
!
interface GigabitEthernet1/0
ip address 10.10.10.246 255.255.255.0
negotiation auto
!
B) Configure R3
1) Setup IKE phase 1 (HAGLE)
crypto isakmp policy 12) Setup IKE phase 2 (IPsec transform)
encr 3des
hash md5
authentication pre-share
group 2
lifetime 10000
!crypto isakmp key mys3cr3t address 1.1.1.1
crypto ipsec transform-set SCLabs-SET esp-aes 2563) Create ACL to match IPSec traffic will be encrypted
access-list 110 permit ip 172.16.0.0 0.0.255.255 10.10.10.0 0.0.0.2554) Create Crypto-map with sequence "10" and linked to outgoing traffic direction (exit interface)
crypto map SCLabs-MAP 10 ipsec-isakmpVerify
description -=vpn to 1.1.1.1 =-
set peer 1.1.1.1
set transform-set SCLabs-SET
match address 110
!
interface GigabitEthernet1/0
ip address 2.2.2.2 255.255.255.0
crypto map SCLabs-MAP
!
interface GigabitEthernet2/0
ip address 172.16.1.1 255.255.255.0
negotiation auto
!
1) Check connectivity
R1#ping 2.2.2.22) After configuration is done, check IPSec tunnel
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 8/8/12 ms
Session is down, because no packets matched to ACL 110. (ping from Step 1 has source IP 1.1.1.1 and not from LAN 10.10.10.0/24)
R1#show crypto session3) Initial some packets from interested LAN (from 10.10.10.0/24 to 172.16.0.0/16)
Crypto session current status
Interface: GigabitEthernet2/0
Session status: DOWN
Peer: 2.2.2.2 port 500
IPSEC FLOW: permit ip 10.10.10.0/255.255.255.0 10.10.10.0/255.255.255.0
Active SAs: 0, origin: crypto map
R1#
R1#ping
Protocol [ip]:
Target IP address: 172.16.1.2
Repeat count [5]:
Datagram size [100]:
Timeout in seconds [2]:
Extended commands [n]: y
Source address or interface: 10.10.10.246
Type of service [0]:
Set DF bit in IP header? [no]:
Validate reply data? [no]:
Data pattern [0xABCD]:
Loose, Strict, Record, Timestamp, Verbose[none]:
Sweep range of sizes [n]:
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.1.2, timeout is 2 seconds:
Packet sent with a source address of 10.10.10.246
...!!
Success rate is 40 percent (2/5), round-trip min/avg/max = 12/22/32 ms
R1#
4) From LAN 10.10.10.0/24, check ping to remote LAN 172.16.1.2
Before IPSec tunnel is UP
C:\Windows\system32>TRACERT.EXE 172.16.1.2After IPSec is UP
Tracing route to 172.16.1.2 over a maximum of 30 hops
1 5 ms 2 ms 1 ms 10.10.10.246
2 5 ms 5 ms 6 ms 1.1.1.2
3 31 ms 10 ms 9 ms 2.2.2.2
4 15 ms 14 ms 13 ms 172.16.1.2
Trace complete.
C:\Windows\system32>TRACERT.EXE -d 172.16.1.25) Check IPSec session again
Tracing route to 172.16.1.2 over a maximum of 30 hops
1 1 ms 2 ms 1 ms 10.10.10.246
2 14 ms 10 ms 10 ms 2.2.2.2
3 15 ms 14 ms 14 ms 172.16.1.2
Trace complete.
R1#show crypto session6) Check MTU path
Crypto session current status
Interface: GigabitEthernet2/0
Session status: UP-ACTIVE
Peer: 2.2.2.2 port 500
IKE SA: local 1.1.1.1/500 remote 2.2.2.2/500 Active
IPSEC FLOW: permit ip 10.10.10.0/255.255.255.0 172.16.0.0/255.255.0.0
Active SAs: 2, origin: crypto map
R1#
R1#show crypto session detail
Crypto session current status
Code: C - IKE Configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal, T - cTCP encapsulation
X - IKE Extended Authentication, F - IKE Fragmentation
Interface: GigabitEthernet2/0
Uptime: 00:03:12
Session status: UP-ACTIVE
Peer: 2.2.2.2 port 500 fvrf: (none) ivrf: (none)
Phase1_id: 2.2.2.2
Desc: (none)
IKE SA: local 1.1.1.1/500 remote 2.2.2.2/500 Active
Capabilities:(none) connid:1003 lifetime:02:43:27
IPSEC FLOW: permit ip 10.10.10.0/255.255.255.0 172.16.0.0/255.255.0.0
Active SAs: 2, origin: crypto map
Inbound: #pkts dec'ed 615 drop 0 life (KB/Sec) 4413817/3407
Outbound: #pkts enc'ed 628 drop 2 life (KB/Sec) 4413817/3407
R1#
C:\tools>mturoute.exe 172.16.1.2
* ICMP Fragmentation is not permitted. *
* Speed optimization is enabled. *
* Maximum payload is 10000 bytes. *
- ICMP payload of 1472 bytes is too big.
....
.+ ICMP payload of 1422 bytes succeeded.
+ ICMP payload of 1425 bytes succeeded.
+ ICMP payload of 1426 bytes succeeded.
- ICMP payload of 1427 bytes is too big.
Path MTU: 1454 bytes.
C:\tools>mtupath.exe 172.16.1.27) Check IPSec on R3
MTU path scan to 172.16.1.2, ttl=64, limit=48
# 16 processing - best MSS 1426 (estimated MTU 1454) [pPPPPpPppPPpPPPp]
#1 MSS IN RANGE 1 <== 1425 ==> 1426
#2 MSS EXCEEDED 1427 <== 14957 ==> 16384
R3#show crypto sess
Crypto session current status
Interface: GigabitEthernet1/0
Session status: UP-ACTIVE
Peer: 1.1.1.1 port 500
IKE SA: local 2.2.2.2/500 remote 1.1.1.1/500 Active
IPSEC FLOW: permit ip 172.16.0.0/255.255.0.0 10.10.10.0/255.255.255.0
Active SAs: 2, origin: crypto map
R3#
8) IKE session config
R1#show crypto isakmp policy9) The show crypto map verifies our IPsec status
Global IKE policy
Protection suite of priority 1
encryption algorithm: Three key triple DES
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #2 (1024 bit)
lifetime: 10000 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R1#
R1#show crypto map10) The show crypto ipsec transform-set verifies our IPsec status and shows that we're using tunnel mode (rather than transport mode).
Crypto Map "SCLabs-MAP" 10 ipsec-isakmp
Description: -=vpn to 2.2.2.2 =-
Peer = 2.2.2.2
Extended IP access list 110
access-list 110 permit ip 10.10.10.0 0.0.0.255 172.16.0.0 0.0.255.255
Current peer: 2.2.2.2
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Transform sets={
SCLabs-Set: { esp-256-aes } ,
}
Interfaces using crypto map SCLabs-MAP:
GigabitEthernet2/0
R1#
R1#show crypto ipsec transform-set
Transform set SCLabs-SET: { esp-256-aes }
will negotiate = { Tunnel, },
Transform set #$!default_transform_set_1: { esp-aes esp-sha-hmac }
will negotiate = { Transport, },
Transform set #$!default_transform_set_0: { esp-3des esp-sha-hmac }
will negotiate = { Transport, },
R1#
11) Show info about IPSec security associations (SAs)
R1#show crypto ipsec sa
interface: GigabitEthernet2/0
Crypto map tag: SCLabs-MAP, local addr 1.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (10.10.10.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.0.0/255.255.0.0/0/0)
current_peer 2.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 623, #pkts encrypt: 623, #pkts digest: 623
#pkts decaps: 612, #pkts decrypt: 612, #pkts verify: 612
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 2.2.2.2
path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet2/0
current outbound spi: 0x539CC616(1402783254)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xC5FDA537(3321734455)
transform: esp-256-aes ,
in use settings ={Tunnel, }
conn id: 7, flow_id: SW:7, sibling_flags 80000046, crypto map: SCLabs-MAP
sa timing: remaining key lifetime (k/sec): (4391197/1001)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x539CC616(1402783254)
transform: esp-256-aes ,
in use settings ={Tunnel, }
conn id: 8, flow_id: SW:8, sibling_flags 80000046, crypto map: SCLabs-MAP
sa timing: remaining key lifetime (k/sec): (4391197/1001)
IV size: 16 bytes
replay detection support: N
Status: ACTIVE
outbound ah sas:
outbound pcp sas:
R1#
R3#show crypto ipsec sa | inc pktsConfiguration with CCP
#pkts encaps: 612, #pkts encrypt: 612, #pkts digest: 612
#pkts decaps: 623, #pkts decrypt: 623, #pkts verify: 623
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
R3#
 |
| Step 1, Site-to-Site VPN Wizard |
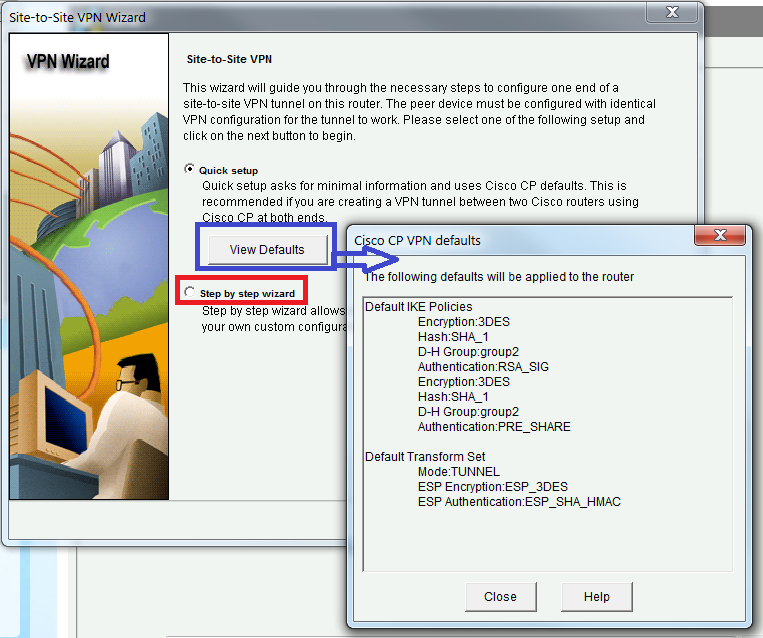 |
| Step 2, Select Step by step wizard |
 |
| Step 3, Configure Peer and Peer authentication |
 |
| Step 4, Configure IKE Phase 1 |
 |
| Step 5, Set Up IPSec settings (transform-set) |
 |
| Step 6, Configure Interesting Traffic (which will be encrypted) |
 |
| Step 7, Final settings review, Press FINISH to complete wizard |
If all parameteres are OK, send config with Delivery option.