Vlan10 192.168.10.1 YES manual up down
- By default, all switch ports in Layer 2 mode are nontrunking and operate as access links
- Ports on the 2960 and 3560 switches are set to dynamic auto by default
This means that they are willing to negotiate a trunk with the neighbor; however, if both sides are set to dynamic auto, the link will remain in access mode
- even when a port is statically (trunk or acces) configured, DTP is still active on the port.
command 'switchport nonegotiate' - disable DISL/DTP completely (ISL/802.1q)
- DTP advertisements (periodic at 30 seconds) include the VTP domain name. A switch won't form a trunk on a DTP-enabled port to a switch advertising a different VTP domain, even if the ports are manually configured in trunking mode
- vlan 10> shutdown - A VLAN can be made locally inactive (does not apply to an SVI)
- vlan 10> state suspend/active - its posible to “suspend” VLAN (causes all ports in that VLAN throughout the VTP domain to stop transferring data)
- encapsulation dot1q <vlan> native - native VLAN is configured on a Router subinterface,
- switchport trunk native vlan 7 - On Switch , traffic from VLAN 7 will go untagged on trunk link.
- Cisco recommends a one-to-one correspondence between VLANs and IP subnets.
This recommendation means that if a subnet with a 24-bit mask (255.255.255.0) is used for a VLAN, no more than 254 devices should be in the VLAN.
- STP and DTP frames have no relation to VLAN, so are always transmited over Native VLAN.
CDP/VTP/PAgP/UDLD are always transmited over VLAN 1, if Native VLAN is 1 then will be transmited in untagged form, if VLAN 1 is tagged (Native VLAN is other VLAN then 1), protocols will be tagged with 1.
DTP defaults:
- dynamic auto (3550)
- dynamic desirable (3560)
- Cat2950 do not support DTP, and it's in a kind of nonnegotiate mode.
nonnegotiate + on (mode trunk) = Trunk
nonnegotiate + nonnegotiate = Trunk
Auto + On = Trunk
and 'off mode', which is best for any kinds of access ports (do not allow to establish trunk connection)
Trunk config example
interface Port-channel1
switchport access vlan 100
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 100,101,172,192
switchport mode trunk
!! int po1 have configs for access and trunk, but only specific config will be active depending on mode set (trunk-active, access- inactive)
switchport nonegotiate
spanning-tree portfast trunk
!
The net result of this configuration is:Switch port Operational Mode
- WHEN the port is in access mode: it will only pass (untagged) traffic on VLAN 100
- WHEN the port is in trunk mode (>1 VLAN):
the port will pass untagged traffic on VLAN 1
the port will pass tagged traffic on VLAN 100,101,172,192
HOWEVER note that VLAN 1 is not in the allowed list > no untagged traffic will be allowed to traverse this port
switchport mode trunk > this port will always be in trunk mode
switchport nonegotiate > do not send DTP frames - such frames may get forwarded incorrectly and cause ports on other switches to negotiate to trunks when they're not supposed to.
you possibly want to add: switchport trunk native vlan 100 if the other end of the link is expecting untagged traffic to be VLAN 100.
SW8(config-if)#do sh int fa 0/6 sw
Name: Fa0/6
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: trunk
SW8(config-if)# int fa 0/6Show trunk interfaces
SW8(config-if)#sh
*Mar 1 01:00:47.165: %LINK-5-CHANGED: Interface FastEthernet0/6, changed state to administratively down
*Mar 1 01:00:48.171: %LINEPROTO-5-UPDOWN: Line protocol on Interface FastEthernet0/6, changed state to down
SW8(config-if)#do sh int fa 0/6 sw
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: down <---interface is shutted down (administratively or link down)
Administrative Trunking Encapsulation: dot1q
Negotiation of Trunking: On
- show interface trunk
- show interface status | in trunk
- show interface Fa1/0/13 switchport
- show interface Fa1/0/13 trunk
S3750-1# sh int status | in trunk
Gi6/1 ... voip1 AS1 connected trunk full 100 10/100/1000-TX
Gi6/1 ... voip2 AS2 connected trunk full 100 10/100/1000-TX
S3750-1# show interface Fa1/0/13 switchport
Name: Fa1/0/13
Switchport: Enabled
Administrative Mode: dynamic desirable
Operational Mode: trunk
S3750-1#show interface trunk
Port Mode Encapsulation Status Native vlan
Fa1/0/13 desirable n-isl trunking 1
Fa1/0/14 desirable n-isl trunking 1
Fa1/0/15 desirable n-isl trunking 1
S3750-1#show interface Fa1/0/13 trunk
Port Mode Encapsulation Status Native vlan
Fa1/0/13 desirable n-isl trunking 1
no ip redirects--this disables
icmp redirect messages. Redirects happen when a router recognizes a
packet arriving on an interface and the best route is out that same
interface. In that case the router sends an icmp redirect back to the
source telling them about a better router on the same subnet. Subsequent
packets take the optimal path. If you disable this, the packets would
have continued using the sub optimal path (in this scenario).
no
ip unreachable--disable icmp type 3 generation. Can wreak havoc if an
egress port has a lower mtu. This is because icmp "packet to big
fragment needed" is type 3 code 4.
no
ip proxy-arp--proxy arp allows the router to respond to any arp request
that is out another interface according to the route table. Disabling
this makes the router only respond to arps to the interface ip address.
no ip route-cache--process switches ip packets. Mostly useful only with debug ip packet.
Port Types (from cisco.com)
Switch Ports
- Switch ports are Layer 2-only interfaces associated with a physical port.
- Switch ports belong to one or more VLANs.
- A switch port can be an access port, a trunk port, or a tunnel port.
- Configure switch ports by using the switchport interface configuration commands.
Access Ports
- An access port belongs to and carries the traffic of only one VLAN (unless it is configured as a voice VLAN port).
- Traffic is received and sent in native formats with no VLAN tagging.
- Traffic arriving on an access port is assumed to belong to the VLAN assigned to the port.
- If an access port receives a tagged packet (Inter-Switch Link [ISL] or IEEE 802.1Q tagged), the packet is dropped, and the source address is not learned.
Trunk Ports
- A trunk port carries the traffic of multiple VLANs and by default is a member of all VLANs in the VLAN database.
- In an ISL trunk port, all received packets are expected to be encapsulated with an ISL header, and all transmitted packets are sent with an ISL header.
Native (non-tagged) frames received from an ISL trunk port are dropped.
- An IEEE 802.1Q trunk port supports simultaneous tagged and untagged traffic. An IEEE 802.1Q trunk port is assigned a default port VLAN ID (PVID), and all untagged traffic travels on the port default PVID.
All untagged traffic and tagged traffic with a NULL VLAN ID are assumed to belong to the port default PVID.
A packet with a VLAN ID equal to the outgoing port default PVID is sent untagged.
All other traffic is sent with a VLAN tag.
Tunnel Ports (QinQ)
- Tunnel ports are used in IEEE 802.1Q tunneling to segregate the traffic of customers in a service-provider network from other customers who are using the same VLAN number.
- Packets entering the tunnel port on the edge switch, already IEEE 802.1Q-tagged with the customer VLANs, are encapsulated with another layer of an IEEE 802.1Q tag (called the metro tag), containing a VLAN ID unique in the service-provider network, for each customer. The double-tagged packets go through the service-provider network keeping the original customer VLANs separate from those of other customers. At the outbound interface, also a tunnel port, the metro tag is removed, and the original VLAN numbers from the customer network are retrieved.
- Tunnel ports cannot be trunk ports or access ports and must belong to a VLAN unique to each customer.
Routed Ports (on MLS)
- routed port is a physical port on MLS that is capable of Layer 3 packet processing (like a port on a router; it does not have to be connected to a router)
- routed port is not associated with a particular VLAN, as contrasted with an access port or SVI.
- routed port as is an access port.
- used when switch has one port per VLAN or subnet.
- routed port behaves like a regular router interface, except that it does not support VLAN subinterfaces.
-- on lower layer Catalyst platforms, you can not create subinterfaces on this port, contrary to routed ports on routers.
-- higher-level Catalyst platforms allow even subinterfaces to be configured on these routed ports (in which case more internal usage VLANs are being created)
- routed ports can be configured with a Layer 3 routing protocol.
- the switch functionality is removed from the interface.
- routed port is a Layer 3 interface only and does not support Layer 2 protocols, such as DTP/VTPSTP.
- configure routed ports by putting the interface into Layer 3 mode with the no switchport interface configuration command.
- can assign an IP address to the port, enable routing, and assign routing protocol characteristics by using the ip routing and router protocol global configuration commands.
- the number of routed ports that you can configure is not limited by software.
Technically, the following configuration:
interface FastEthernet0/23is identical to:
no switchport
ip address 192.0.2.1 255.255.255.0
interface FastEthernet0/23assuming the VLAN 1006 is the internal VLAN allocated for this port.
switchport mode access
switchport access vlan 1006
switchport nonegotiate
spanning-tree bpdufilter enable
spanning-tree portfast
no vtp
!
interface Vlan 1006
ip address 192.0.2.1 255.255.255.0
!
Routed ports are simply a "hack" - instead of manually creating a separate VLAN, assigning a single port to it, deactivating some of the L2 management protocols on the port, creating a SVI for that VLAN and performing all IP-related configuration on the SVI, the no switchport command simply makes it possible for you to configure the same functionality directly on a physical port with less hassle - but the internal processing does not change.
Switch Virtual Interfaces - SVI
- A switch virtual interface (SVI) represents a VLAN of switch ports as one interface to the routing or bridging function in the system.
- Only one SVI can be associated with a VLAN, but you need to configure an SVI for a VLAN only when you wish to route between VLANs, to fallback-bridge nonroutable protocols between VLANs, or to provide IP host connectivity to the switch. By default, an SVI is created for the default VLAN (VLAN 1) to permit remote switch administration.
- Additional SVIs must be explicitly configured.
- You cannot delete interface VLAN 1.
- You can configure routing across SVIs
- Configure a VLAN interface for each VLAN for which you want to route traffic, and assign it an IP address.
SVI autostate
from http://packetlife.net/blog/2009/nov/9/svi-autostate/
Cisco IOS SVIs, also called VLAN interfaces, exhibit what might be considered an odd behavior: by default, an SVI will show an interface state of up but a line protocol state of down.
Switch# show ip interface briefThis is because an SVI must meet all of the following conditions to transition to the full "up/up" state:
Interface IP-Address OK? Method Status Protocol
Vlan1 unassigned YES unset administratively down down
Vlan10 192.168.10.1 YES manual up down
- Its VLAN must exist and be active in the VLAN database.
- At least one switched port in the VLAN (access or trunk) must be up.
- That port must be in the STP forwarding state.
The idea is to bring the Layer 3 interface down so that routing protocols will cease advertising a route to the IP subnet if there are no active switch interfaces on the VLAN where the subnet exists.
Typically, a newly created VLAN will not yet have been assigned to any ports. Once it is, and provided at least one of those ports is operational, we see the SVI line protocol transition to the up state:
Switch(config)# interface f0/3Cisco refers to this behavior as autostate. While usually very handy, this behavior might not always be desirable. For example, an engineer might wish for an SVI to always remain up so that a can be reached via its associated IP address even if all ports associated with that VLAN are down (or if the VLAN itself has gone missing).
Switch(config-if)# switchport access vlan 10
Switch(config-if)#
LINEPROTO-5-UPDOWN: Line protocol on Interface Vlan10, changed state to up
- In some IOS releases, you can exclude the individual physical ports from the autostate calculation with the switchport autostate exclude interface configuration command. Most commonly you’d want to exclude uplink ports on access switches.
- In some unspecified IOS releases (including 12.4T), you can use the (currently undocumented according to Command Lookup Tool) no autostate VLAN interface configuration command, which disables the autostate algorithm and makes the SVI interface permanently active.
The SVI Autostate exclude feature shuts down (or brings up) the Layer 3 interfaces of a switch when the following port configuration changes occur:
- When the last port on a VLAN goes down, the Layer 3 interface on that VLAN is shut down (SVI- autostated).
- When
the first port on the VLAN is brought back up, the Layer 3 interface on
the VLAN that was previously shut down is brought up.
SVI Autostate exclude enables you to exclude the access ports/trunks in
defining the status of the SVI (up or down) even if it belongs to the
same VLAN. Moreover, even if the excluded access port/trunk is in up
state and other ports are in down state in the VLAN, the SVI state is
changed to down.
At least one port in the VLAN should be up and not excluded to make the
SVI state "up." This will help to exclude the monitoring port status
when you are determining the status of the SVI.
Switch(config)# interface <interface-id>
Switch(config-if)# switchport autostate exclude
Switch(config)# end
Switch# show int g3/4 switchport
VLANs
A full Layer 2–only switched network is referred to as a flat network topology. A flat network is a single broadcast domain, such that every connected device sees every broadcast packet that is transmitted.
A switched environment offers the technology to overcome flat network limitations.
Switched networks can be subdivided into VLANs. By definition, a VLAN is a single broadcast domain..
Devices connected to a different VLAN will not receive those same broadcasts.
VLAN Membership
Two membership methods exist on Cisco Catalyst switches:
■ Static VLAN configuration - provide port-based membership, No handshaking or unique VLAN membership protocol is needed for the end devices; they automatically assume VLAN connectivity when they connect to a port.
Normally, the end device is not even aware that the VLAN exists.
The static port-to-VLAN membership normally is handled in hardware with applicationspecific integrated circuits (ASIC) in the switch.
■ Dynamic VLAN assignment - provide membership based on the MAC address of an end-user device.
When a port is configured as "dynamic," it receives VLAN information based on the MAC-address that is on the port. The VLAN is not statically assigned to the port; it is dynamically acquired from the VMPS based on the MAC-address on the port.
- Devices are in the same VLANregardless of which port they are attached to.
When the link becomes active, the switch does not forward traffic to or from this port until the port is assigned to a VLAN. The source MAC address from the first packet of a new host on the dynamic port is sent to the VMPS as part of the VQP request, which attempts to match the MAC address to a VLAN in the VMPS database. If there is a match, the VMPS sends the VLAN number for that port. If there is no match, the VMPS either denies the request or shuts down the port (depending on the VMPS security mode setting).
- Multiple hosts (MAC addresses) can be active on a dynamic port if all are in the same VLAN. If the link goes down on a dynamic port, the port returns to the unassigned state and does not belong to a VLAN. Any hosts that come online through the port are checked again with the VMPS before the port is assigned to a VLAN.
- A maximum of 50 hosts are supported on a given port at any given time. Once this maximum is exceeded, the port is shut down, irrespective of the operating mode of the VMPS server.
Switch(config)# interface fa1/1One important factor we haven't yet mentioned is that you cannot run the VMPS server on a Cisco Catalyst 2900 or 3500 series. The Catalyst 4500 and upwards are able to act as a VMPS,
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan dynamic
Configuring Static VLANs
By default, all switch ports are assigned to VLAN 1, are set to be a VLAN type of Ethernet, and have a maximum transmission unit (MTU) size of 1500 bytes.
First, the VLAN must be created on the switch, if it does not already exist.
Then, the VLAN must be assigned to specific switch ports.
VLANs 1 and 1002 through 1005 automatically are created and are set aside for special uses. For example, VLAN 1 is the default VLAN for every switch port. VLANs 1002 to 1005 are reserved for legacy functions related to Token Ring and FDDI switching.
Catalyst IOS switches also can support extended-range VLANs, in which the VLAN number can be 1 to 4094, for compatibility with the IEEE 802.1Q standard.
Tip: Although the extended range of VLAN numbers enables you to support more VLANs in your network, some limitations exist..
The VLAN Trunking Protocol (VTP) uses the VLAN database so that VLAN definitions can be advertised and shared between switches over trunk links. When extended-range VLANs are created, they are not stored in the VLAN database file.
1. Create VLAN
Switch(config)# vlan <vlan-number>2. Assign VLAN on interface
Switch(config-vlan)# name <vlan-name>
Example
Switch(config)# vlan 2
Switch(config-vlan)# name Engineering
Switch(config)# interface type module/numberBy default, every Catalyst IOS switch port is ready for Layer 3 operation, something that doesn’t coexist with Layer 2 VLANs.
Switch(config-if)# switchport <!--- configures the port for Layer 2 operation
Switch(config-if)# switchport mode access
Switch(config-if)# switchport access vlan <vlan-num>
Verify VLAN
show vlanDynamic VLANs
VLAN Name Status Ports
---- ---------------------------------- ------ -------------------------------1 default active Gi1/1, Gi1/2, Gi3/20, Gi4/20
2 Engineering active Gi4/2, Gi4/3, Gi4/4, Gi4/5
Gi4/6, Gi4/7, Gi4/8, Gi4/9
Gi4/10, Gi4/11, Gi4/12
101 Marketing active Gi2/5, Gi2/6, Gi2/7, Gi2/8
Gi2/9, Gi2/10, Gi2/11, Gi2/12
Dynamic VLANs provide membership based on the MAC address of an end-user device.
A network administrator also must assign the user’s MAC address to a VLAN in the database of a VLAN Membership Policy Server (VMPS).
With Cisco switches, dynamic VLANs are created and managed using network-management tools such as CiscoWorks.
Deploying VLANs
Cisco recommends a one-to-one correspondence between VLANs and IP subnets.
This recommendation means that if a subnet with a 24-bit mask (255.255.255.0) is used for a VLAN, no more than 254 devices should be in the VLAN. I
End-to-end VLANs,
- also called campuswide VLANs, span the entire switch fabric of a network.
- are positioned to support maximum flexibility and mobility of end devices.
- users can be assigned to VLANs regardless of their physical location.
- 80/20 rule - estimates that 80 percent of user traffic stays within the local workgroup, whereas 20 percent is destined for a remote resource in the campus network.
- Because all VLANs must be available at each access-layer switch, VTP must be used to carry all VLANs between the access- and distribution-layer switches.
- End-to-end VLANs are not recommended in an enterprise network, unless there is a good reason.
Local VLANs
- most enterprise networks have moved toward the 20/80 rule (where server and intranet/Internet resources are centralized), end-to-end VLANs have become cumbersome (heavy) and difficult to maintain.
- 20/80 rule reverses the traffic pattern of the end-to-end VLAN: Only 20 percent of traffic is local, whereas 80 percent is destined to a remote resource across the core layer.
- Local or geographic VLANs range in size from a single switch in a wiring closet to an entire building. This scenario provides maximum availability by using multiple paths to destinations, maximum scalability by keeping the VLAN within a switch block, and maximum manageability.
VLAN Trunks
A trunk link, however, can transport more than one VLAN through a single switch port.
Trunk links are most beneficial when switches are connected to other switches or switches are connected to routers.
Connecting two switches with separate physical links for each VLAN is possible.
- Tag the data frame with VLAN information and recalculate FCS
The frame check sequence (FCS) is a 4-octet cyclic redundancy check which allows detection of corrupted data within the entire frame.
VLAN Frame Identification
Frame identification, or tagging, assigns a unique user-defined ID to each frame transported on a trunk link.
Think of this ID as the VLAN number or VLAN “color,” as if each VLAN were drawn on a network diagram in a unique color.
VLAN identification can be performed using two methods, each using a different frame identifier mechanism:
■ Inter-Switch Link (ISL) protocol
■ IEEE 802.1Q protocol
 |
| VLAN Taggings |
VLAN Header
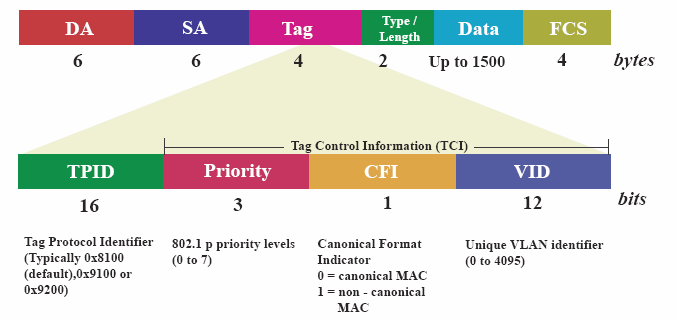 |
| VLAN Header info |
* TCI (Tag Control Information) field including user priority, Canonical format indicator and VLAN ID.
- User Priority - Defines user priority, giving eight (2^3) priority levels (from 0 to 7). IEEE 802.1P defines the operation for these 3 user priority bits.
- Drop eligible indicator (DEI): a 1-bit field. (formerly CFI) May be used separately or in conjunction with PCP to indicate frames eligible to be dropped in the presence of congestion.
old: CFI- Canonical Format Indicator is always set to zero for Ethernet switches. CFI is used for compatibility reason between Ethernet type network and Token Ring type network. If a frame received at an Ethernet port has a CFI set to 1, then that frame should not be forwarded as it is to an untagged port.
- VID - VLAN ID is the identification of the VLAN, which is basically used by the standard 802.1Q. It has 12 bits and allow the identification of 4096 (2^12) VLANs. Of the 4096 possible VIDs, a VID of 0 is used to identify priority frames and value 4095 (FFF) is reserved, so the maximum possible VLAN configurations are 4,094.
Additional Info:
For CVLAN TPID = 8100 , CFI - Canonical Format Indicator
For SVLAN TPID = 88a8 , DEI - Drop Eligible Inidicator
Cisco switches drop the packet, If CFI=1 but Carrier Ethernet switch (Fujitsu) does not drop the packet and uses it mark the packet as per 802.1p.
Inter-Switch Link Protocol
Is a Cisco-proprietary protocol for preserving the source VLAN identification of frames passing over a trunk link.
Any Cisco switch or router device configured for ISL can process and understand the ISL VLAN information.
The ISL method of VLAN identification or trunking encapsulation no longer is supported across all Cisco Catalyst switch platforms.
Sw(config-if)# switchport trunk encapsulation isl
IEEE 802.1Q (dot1.q) Protocol
This frame-identification method is standardized, allowing VLAN trunks to exist and operate between equipment from multiple vendors.
However, instead of encapsulating each frame with a VLAN ID header and trailer (like in ISL), 802.1Q embeds its tagging information within the Layer 2 frame.
802.1Q also introduces the concept of a native VLAN on a trunk (Frames belonging to this VLAN are notencapsulated with any tagging information).
12 bits are used as a VLAN identifier (VID) to indicate the source VLAN for the frame. The VID can have values from 0 to 4095, but VLANs 0, 1, and 4095 are reserved.
You will not see tags on access port or trunk port with only native vlan;
ISL adds a total of 30 bytes to each frame, whereas 802.1Q adds 4 bytes. Because Ethernet frames cannot exceed 1518 bytes, the additional VLAN tagging information can cause the frame to become too large. Frames that barely exceed the MTU size are called baby giant frames. Switches usually report these frames
as Ethernet errors or oversize frames.
To properly handle and forward them anyway, Catalyst switches use proprietary hardware (for 802.1Q) encapsulation, switches can comply with the IEEE 802.3ac standard, which extends the maximum frame length to 1522 bytes.
Dynamic Trunking Protocol (DTP)
You can manually configure trunk links on Catalyst switches for either ISL or 802.1Q mode. In addition, Cisco has implemented a proprietary, point-to-point protocol called Dynamic Trunking Protocol (DTP)that negotiates a common trunking mode between two switches.
- A trunk link can be negotiated between two switches only if both switches belong to the same VLAN Trunking Protocol (VTP) management domain or if one or both switches have not defined their VTP domain (that is, the NULL domain).
- You should disable DTP negotiation if a switch has a trunk link connected to a nontrunking router or firewall interface because those devices cannot participate in DTP negotiation.
- If the two switches are in different VTP domains and trunking is desired between them, you must set the trunk links to on mode or nonegotiate mode.
SW-4500#sh dtp
Global DTP information
Sending DTP Hello packets every 30 seconds
Dynamic Trunk timeout is 300 seconds
109 interfaces using DTP
SW-4500#
SW-4500#sh dtp interface
DTP information for GigabitEthernet1/1:
TOS/TAS/TNS: ACCESS/OFF/ACCESS
TOT/TAT/TNT: UNKNOWN/NEGOTIATE/UNKNOWN
Neighbor address 1: 000000000000
Neighbor address 2: 000000000000
Hello timer expiration (sec/state): never/STOPPED
Access timer expiration (sec/state): never/STOPPED
Negotiation timer expiration (sec/state): never/STOPPED
Multidrop timer expiration (sec/state): never/STOPPED
FSM state: S1:OFF
# times multi & trunk 0
Enabled: no
In STP: no
Statistics
----------
0 packets received (0 good)
0 packets dropped
0 nonegotiate, 0 bad version, 0 domain mismatches,
0 bad TLVs, 0 bad TAS, 0 bad TAT, 0 bad TOT, 0 other
1 packets output (1 good)
1 native, 0 software encap isl, 0 isl hardware native
0 output errors
0 trunk timeouts
0 link ups
1 link downs, last link down on Thu Oct 25 2012, 09:33:23
VLAN Trunk Configuration
A switch port must be in Layer 2 mode before it can support a trunk.
Switch(config)# interface <type mod/port>By default, an 802.1Q trunk uses VLAN 1 as the native VLAN.
Switch(config-if)# switchport <--- A switch port must be in Layer 2 mode before it can support a trunk
Switch(config-if)# switchport trunk encapsulation {isl | dot1q | negotiate}
Switch(config-if)# switchport trunk native vlan vlan-id <--- identifying the untagged or native VLAN
Switch(config-if)# switchport trunk allowed vlan {vlan-list | all | {add | except | remove} vlan-list}
Switch(config-if)# switchport mode {trunk | dynamic {desirable | auto}}
In the case of an ISL trunk, using this command has no effect because ISL doesn’t support an untagged VLAN.
switchport trunk allowed vlan:
■ vlan-list—An explicit list of VLAN numbers, separated by commas or dashes.
■ all—All active VLANs (1 to 4094) will be allowed.
■ add vlan-list—A list of VLAN numbers will be added to the already configured list; this is a shortcut to keep from typing a long list of numbers.
■ except vlan-list—All VLANs (1 to 4094) will be allowed, except for the VLAN numbers listed; this is a shortcut to keep from typing a long list of numbers.
■ remove vlan-list—A list of VLAN numbers will be removed from the already configured list; this is a shortcut to keep from typing a long list of numbers.
switchport mode:
■ trunk—permanent unconditional trunking mode without any negotiation. DTP is still operational, so if the far-end switch port is configured to trunk, dynamic desirable, or dynamic auto mode, trunking will be negotiated successfully. The corresponding switch port at the other end of the trunk should be configured similarly. In this way, both switches always expect the trunk link to be operational without any negotiation.
■ dynamic desirable (the default)—The port actively attempts to convert the link into trunking mode. If the far-end switch port is configured to trunk, dynamic desirable, or dynamic auto mode, trunking is negotiated successfully.
■ dynamic auto—The port can be converted into a trunk link, but only if the far-end switch actively requests it. Therefore, if the far-end switch port is configured to trunk or dynamic desirable mode, trunking is negotiated.
Because of the passive negotiation behavior, the link never becomes a trunk if both ends of the link are left to the dynamic auto default.
In all these modes, DTP frames are sent out every 30 seconds to keep neighboring switch ports informed of the link’s mode.
switchport nonegotiate - disable Dynamic InterSwitch Link Protocol (DISL) and DTP completely (frames are not exchanged) - if you decide to configure both ends of a trunk link as a fixed trunk (switchport modetrunk).
Switch# show interface gigabitethernet 2/1 trunk
Port Mode Encapsulation Status Native vlan
Gi2/1 on 802.1q trunking 1
Trunk example configuration
Switch-D(config)# interface gigabitethernet 2/1
Switch-D(config-if)# switchport trunk encapsulation dot1q
Switch-D(config-if)# switchport trunk native vlan 100
Switch-D(config-if)# switchport trunk allowed vlan 100-105
Switch-D(config-if)# switchport mode dynamic desirable
Switch-D# show interface gigabitethernet 2/1 trunk
Port Mode Encapsulation Status Native vlan
Gi1/1 desirable 8 02.1q not-trunking 100
VLAN 103 should not be passed between these switches. (pruning)
Switch-D(config-if)# switchport trunk allowed vlan remove 103
Switch A must be set
Switch-A(config-if)# switchport mode dynamic desirable
Troubleshooting VLANs and Trunks
show vlan id <vlan-id>
show interface <type mod/num> switchport
show interface <type mod/num> trunk
SW-4500#show dtp
Global DTP information
Sending DTP Hello packets every 30 seconds
Dynamic Trunk timeout is 300 seconds
109 interfaces using DTP
SW-4500#
Before the trunk can operate correctly, parameters must be agreeable on both ends■ Trunking mode (unconditional trunking, negotiated, or non-negotiated).
■ Trunk encapsulation (ISL, IEEE 802.1Q, or negotiated through DTP).
■ Native VLAN. (switches will log error messages about the mismatch) - Trunk will form even if the native vlans are different, however both switch will log native vlan mismatch error messages if dot1q is used. To function properly you migth want to set the native vlan to the same value (recommended) but the trunk will form anyway.
■ The native VLAN mismatch is discovered through the exchange of CDP messages,
■ Allowed VLANs. By default, a trunk allows all VLANs to be transported across it. If one end of the trunk is configured to disallow a VLAN, that VLAN will not be contiguous across the trunk.
*Oct 12 04:12:39.794: %CDP-4-NATIVE_VLAN_MISMATCH: Native VLAN mismatch discovered on Ethernet0/1 (1), with IOU10 Ethernet0/1 (666).
Ethernet0/1 (1) - local switch has native of 1
Ethernet0/1 (666) - remote switch has native vlan = 666
SW-4500#sh interface GigabitEthernet6/8 switchport
Name: Gi6/8
Switchport: Enabled
Administrative Mode: trunk
Operational Mode: trunk
Administrative Trunking Encapsulation: dot1q
Operational Trunking Encapsulation: dot1q
Negotiation of Trunking: On
Access Mode VLAN: 1 (default)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Voice VLAN: none
Administrative private-vlan host-association: none
Administrative private-vlan mapping: none
Administrative private-vlan trunk native VLAN: none
Administrative private-vlan trunk Native VLAN tagging: enabled
Administrative private-vlan trunk encapsulation: dot1q
Administrative private-vlan trunk normal VLANs: none
Administrative private-vlan trunk private VLANs: none
Operational private-vlan: none
Trunking VLANs Enabled: 168,199,600,999
Pruning VLANs Enabled: 2-1001
Capture Mode Disabled
Capture VLANs Allowed: ALL
Unknown unicast blocked: disabled
Unknown multicast blocked: disabled
Appliance trust: none
SW-4500#
SW-4500#sh interface GigabitEthernet6/8 trunk
Port Mode Encapsulation Status Native vlan
Gi6/8 on 802.1q trunking 1
Port Vlans allowed on trunk
Gi6/8 16,19,60,99
Port Vlans allowed and active in management domain
Gi6/8 16,19,60,99
Port Vlans in spanning tree forwarding state and not pruned
Gi6/8 16,19,60,99
SW-4500#
MultiVLAN
http://www.cisco.com/c/en/us/support/docs/lan-switching/vlan/10023-3.html#xl
- The multiVLAN port feature on Catalyst 2900XL/3500XL Switches allows you to configure a single port in two or more VLANs.
- This feature allows users from different VLANs to access a server or router without the implementation of inter-VLAN routing capability.
- A multiVLAN port performs normal switching functions in all of its assigned VLANs. VLAN traffic on the multi-VLAN port is not encapsulated as it is in trunking.
- Port hardware is set as an 802.1Q trunk
These are the limitations to the implementation of multi-VLAN port features:
- You cannot configure a multi-VLAN port when a trunk is configured on the switch. You can connect the multi-VLAN port only to a router or server. The switch automatically transitions to VTP transparent mode when the multi-VLAN port feature is enabled, which disables the VTP. No VTP configuration is necessary.
- The multi-VLAN port feature is supported only on Catalyst 2900XL/3500XL Series Switches. This feature is not supported on Catalyst 4500/4000, 5500/5000, or 6500/6000 Series Switches or any other Catalyst switches.
6-3512xl(config)#interface fastethernet 0/1Verify
6-3512xl(config-if)#switchport multi vlan 1,2,3
!--- This command assigns VLANs 1, 2, and 3 to multi-VLAN port Fast Ethernet 0/1.
6-3512xl#show interface fastethernet 0/1 switchportMulti-VLAN mode was never well supported, and had a bunch of restrictions, one of which is what you see, no multi-vlans if any trunk port exists. I assume they did this for security purposes, although it could have been an internal implementation limitation.
Name: Fa0/1
Operational Mode: multi
!--- The port is in multi-VLAN mode.
Cisco dropped multi-vlan mode after this switch model was EOL'd, and no other cisco switches since have supported it.
QinQ (802.Q tunneling)
IEEE 802.1ad is an Ethernet networking standard informally known as QinQ and is an amendment to IEEE standard IEEE 802.1Q-1998.
The technique is also known as provider bridging, Stacked VLANs, or simply QinQ or Q-in-Q. "Q-in-Q" can for supported devices apply to C-tag stacking on C-tag (Ethernet Type = 0x8100) but this has limited application in the modern methodology of network routing.
For VLANs the value in this field is, in large part, determined by the switch's port's configuration.
| VLAN type | EtherType value | tag type | port type | note |
| none | per protocol | untagged frame | access port | IP = 0x800, ARP = 0x0806, etc |
| customer | 0x8100 | tagged frame | 802.1q VLAN trunk port | 802.1q VLAN tagging |
| service | 0x88a8 | QinQ tagged frame | 802.1ad (QinQ) VLAN trunk port | 8021.ad provider tunnel |
For 802.1q VLANs and 802.ad QinQ VLANs the EtherType is actually a "Tag Protocol Identifier (TPID)" that, along with other tagging information, is inserted after the frame's source MAC address field.
 |
| http://groups.geni.net/geni/wiki/QinqResults |
| use | header size | tag size | MTU | FCS | total frame size |
| standard ethernet | 14 | 0 | 1500 | 4 | 1518 |
| 802.1q VLAN trunk | 14 | +4 | 1500 | 4 | 1522 |
| 802.1ad (QinQ) VLAN "tunnel" | 14 | +4 +4 | 1500 | 4 | 1526 |
IEEE 802.1ad was created for the following reasons:
- Provides a simple Layer 2 VPN solution for small-sized MANs or intranets.
- 802.1Q has a 12-bit VLAN ID field, which has a theoretical limit of 212=4096 tags. With the growth of networks, this limitation has become more acute. A double-tagged frame has a theoretical limitation of 4096×4096=16777216, sufficient to accommodate network growth for the next several years.
- The addition of a second tag allows operations that would not have been available had the VLAN ID field simply been expanded from 12 bits to 24 bits (or any other large value). Having multiple tags—the tag stack—allows switches to more easily modify frames. In a tag stack scheme, switches can add ("push"), remove ("pop") or modify single or multiple tags.
- A multi-tagged frame not only has multiple VLAN IDs, but has multiple VLAN header bit fields.
- A tag stack creates a mechanism for Internet Service Providers to encapsulate customer single-tagged 802.1Q traffic with a single tag, the final frame being a QinQ frame. The outer tag is used to identify and segregate traffic from different customers; the inner tag is preserved from the original frame.
- QinQ frames are convenient means of constructing Layer 2 tunnels, or applying Quality of service (QoS) policies, etc.
- 802.1ad is upward compatible with 802.1Q. Although 802.1ad is limited to two tags, there is no ceiling on the standard limiting a single frame to more than two tags, allowing for growth in the protocol. In practice Service Provider topologies often anticipate and utilize frames having more than two tags.
- It is easier for networking equipment makers to modify their existing equipment by creating multiple 802.1Q headers than to modify their equipment to implement some hypothetical new non-802.1Q extended VLAN ID field header.
How QinQ works
- In Q-in-Q tunneling, as a packet travels from a customer VLAN (C-VLAN will be inner vlan) to a service provider's or data center VLAN (S-VLAN will be outer vlan), another 802.1Q tag for the appropriate S-VLAN is added before the C-VLAN tag. The C-VLAN tag remains and is transmitted through the network. As the packet leaves the S-VLAN in the downstream direction, the S-VLAN 802.1Q tag is removed.
- An interface can be a member of multiple S-VLANs. You can map one C-VLAN to one S-VLAN or multiple C-VLANs to one S-VLAN.
- Q-in-Q tunneling does not affect any class-of-service (CoS) values that are configured on a C-VLAN. These settings are retained in the C-VLAN tag and can be used after a packet leaves an S-VLAN. CoS values are not copied from C-VLAN tags to S-VLAN tags.
- The switch prompt to change my MTU to 1504 & reload the switch.
QinQ Configuration
PC1 <-access-> SW1_Access <-802.1q-> SW1_ISP <=QinQ=> SW2_ISP <-802.1q-> SW1_Access <-access-> PC2Config samples
vlan3 trunk vlan34 dot1q-tunnel trunk vlan3
SW1_Access
!
interface GigabitEthernet0/1
description uplink-to-ISP
switchport trunk encapsulation dot1q
switchport mode trunk
!
interface GigabitEthernet0/5
description link-to-PC1
switchport access vlan 3
!
SW1_ISP
!
interface FastEthernet0/1
description downlink-to-client-SW
switchport access vlan 34
switchport mode dot1q-tunnel
!
interface FastEthernet0/2
description QinQ-tunnel-to-SW2_ISP
switchport trunk encapsulation dot1q
switchport mode trunk
!
QinQ Considerations
- Tag customers native VLAN traffic into the QinQ VLAN (vlan dot1q tag native)
- Switches sending/receiving QinQ frames must increase their system MTU to 1504 for VLAN tunneling work. You can check your MTU using #show system mtu. You can increase your MTU by issuing #system mtu 1504, however, this change requires a reboot.
- Tunnel the customer’s CDP, STP, VTP, and CoS values by using the following commands:
Configuring Layer 2 Protocol Tunneling - Protocol tunneling is disabled by default but can be enabled for the individual protocols on IEEE 802.1Q tunnel ports or access ports.
interface GigabitEthernet0/1Sample output
l2protocol-tunnel cdp
l2protocol-tunnel stp
l2protocol-tunnel vtp
l2protocol-tunnel cos
l2protocol-tunnel point-to-point pagp
l2protocol-tunnel point-to-point lacp
l2protocol-tunnel point-to-point udld
no cdp enable <----must be disabled
Switch# show l2protocol-tunnel
COS for Encapsulated Packets: 5
Drop Threshold for Encapsulated Packets: 0
Port Protocol Shutdown Drop Encapsulation Decapsulation Drop
Threshold Threshold Counter Counter Counter
---------- -------- --------- --------- ------------- ------------- -------------
Gi0/1 cdp ---- ---- 10 0 0
stp ---- ---- 292 0 0
vtp ---- ---- 0 0 0
pagp ---- ---- 0 0 0
lacp ---- ---- 0 0 0
udld ---- ---- 0 0 0
QinQ commands
show dot1q-tunnel <---Display 802.1Q tunnel ports on the switch.
show dot1q-tunnel interface <interface-id> <---Verify if a specific interface is a tunnel port.
show l2protocol-tunnel <---Display information about Layer 2 protocol tunneling ports.
show errdisable recovery <---Verify if the recovery timer from a Layer 2 protocol-tunnel error disable state is enabled.
show l2protocol-tunnel interface <interface-id> <---Display information about a specific Layer 2 protocol tunneling port.
show l2protocol-tunnel summary <---Display only Layer 2 protocol summary information.
show vlan dot1q native <---Display the status of native VLAN tagging on the switch.
