Prepare to CCNA Security exam and test Cisco ASA appliance on VmWare ESXi infrastructure.
ASDM java workaround
ASA mgmt ip: 10.10.10.15
download https://10.10.10.15/admin/public/asdm.jnlp
C:\Users\sc>javaws C:\Users\sc\Downloads\asdm.jnlp
show isa sa
show cry ipsec sa
show vpn-sessiondb detail l2l
debug crypto isakmp 7
debug crypto ipsec 7
debug crypto condition peer <peer IP>
un all
clear crypto ipsec sa
clear crypto isakmp sa
!
interface Management0/0
management-only
nameif mgmt
security-level 0
ip address 10.200.200.17 255.255.255.0
!
user-identity default-domain LOCAL
aaa authentication http console LOCAL
aaa authentication ssh console LOCAL
aaa authentication telnet console LOCAL
http server enable
http 10.10.10.0 255.255.255.0 mgmt
username scp password pg94qEe@#$87hXXJ encrypted privilege 15
Install
1. Select ESXi host
2. File -> Deploy OVF Template
3. Select OVF (there are OVF templates over the Internets)
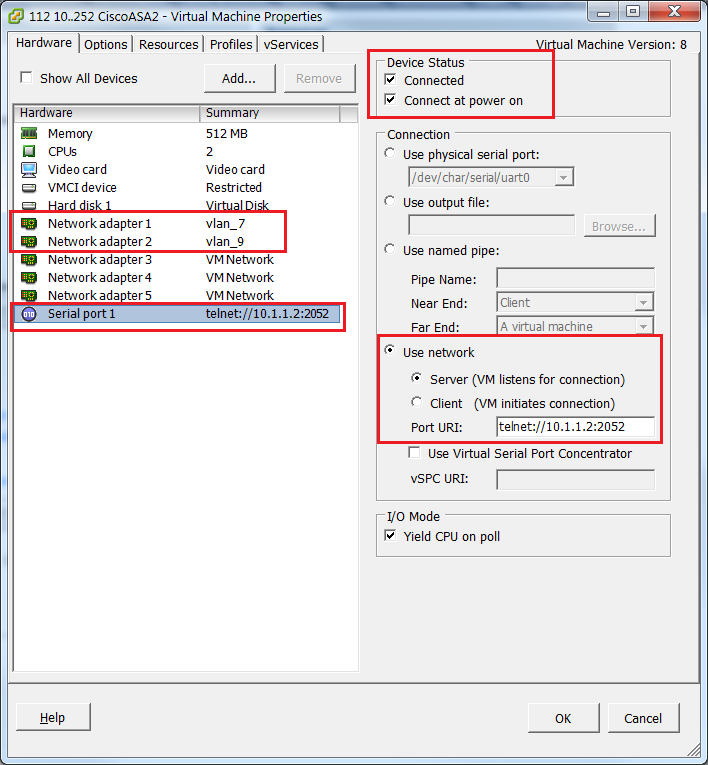
Add Serial Port (Network Based) to redirect Console Port.
Start VM and connect to telnet IP 10.1.1.2 (ESXi host mgmt IP) port 2052.
Cisco ASA IOS is loading
Initializing cgroup subsys cpuBasic Config
Linux version 2.6.29.6 (builders@bld-releng-05a) (gcc version 4.3.4 (crosstool-NG-1.5.0) ) #1 PREEMPT Wed Jun 15 17:19:01 MDT 2011
...
Starting network...
dosfsck 2.11, 12 Mar 2005, FAT32, LFN
Starting check/repair pass.
Starting verification pass.
/dev/hda1: 48 files, 10090/65443 clusters
...
This platform has an ASA 5520
Cisco Adaptive Security Appliance Software Version 8.4(2)
0. Reset Config
write erasePreconfiguration
Erase configuration in flash memory? [confirm]
...
Process shutdown finished
Rebooting.....
Restarting system.
machine restart
...
Pre-configure Firewall now through interactive prompts [yes]? no
Type help or '?' for a list of available commands.
ciscoasa>
Password: (exec password is not set - just press enter)
ciscoasa#
1. Interfaces
ciscoasa(config)# interface GigabitEthernet02. Hostname and DNS
ciscoasa(config-if)# nameif inside
INFO: Security level for "inside" set to 100 by default.
ciscoasa(config-if)# security-level 100
ciscoasa(config-if)# ip address 10.2.1.252 255.255.255.0
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# !
ciscoasa(config-if)# !
ciscoasa(config-if)# interface GigabitEthernet1
ciscoasa(config-if)# nameif outside
INFO: Security level for "outside" set to 0 by default.
ciscoasa(config-if)# security-level 0
ciscoasa(config-if)# ip address 1.1.1.43 255.255.255.192
ciscoasa(config-if)# no shutdown
ciscoasa(config-if)# mtu inside 1500
ciscoasa(config-if)# mtu outside 1500
ciscoasa(config-if)# hostname esx1-asa23. Enable/VTY Passwords
esx1-asa2(config)# domain-name mydmn.com
esx1-asa2(config)# dns domain-lookup outside
esx1-asa2(config)# dns server-group DefaultDNS
esx1-asa2(config-dns-server-group)# name-server 8.8.8.8
esx1-asa2(config-dns-server-group)# name-server 8.8.4.4
esx1-asa2(config-dns-server-group)# domain-name mydmn.com
! Enables password encryption4. Set Telnet Acces and Tune timers
key config-key password-encryption s0m3-encryt3d-t3kst
password encryption aes
! password to Privilege EXEC (IOS enable secret)
enable password <password>
enable password pas@#E!dc
! The login password is used for Telnet and SSH connections.
{passwd | password} <password>
passwd DV#F#$FD4f$
telnet 10.1.1.0 255.255.255.0 insideTo start SSH
telnet timeout 15
ssh timeout 15
console timeout 0
esx1-asa2(config)# crypto key generate rsa modulus 10245. Set Time and NTP
INFO: The name for the keys will be: <Default-RSA-Key>
Keypair generation process begin. Please wait...
esx1-asa2(config)# ssh 10.1.1.0 255.255.255.0 inside
esx1-asa2(config)# ssh version 2
esx1-asa2(config)# ssh timeout 15
clock timezone EEST 26. Setup Acces to Cisco ASDM
clock summer-time EEDT recurring last Sun Mar 3:00 last Sun Oct 4:00
ntp server 10.1.1.4
ntp server 10.1.1.1
http server enable7. Set Default Gateway
http 10.1.1.0 255.255.255.0 inside
route outside 0.0.0.0 0.0.0.0 2.3.4.5 18. Setup Users
esx1-asa2(config)# username sc password ********* privilege 159. Setup SNMP
Minimum allowed username length is 3
ERROR: Username addition failed.
esx1-asa2(config)# username sclabs password ********* privilege 15
! use the local database as your main method of authentication with no fallback. In order to do this, enter LOCAL alone
(config)#aaa authentication ssh console LOCAL
esx1-asa2(config)# snmp-server host inside 10.1.1.42 community ***** version 2c10. Apply activate keys
esx1-asa2(config)# snmp-server community *****
esx1-asa2(config)# snmp-server location ESX1-location
esx1-asa2(config)# snmp-server contact noc@mydmn.com
esx1-asa2(config)# logging buffered notifications
esx1-asa2(config)# logging buffer-size 1048576
11. Save config and reload
esx1-asa2(config)# wr
Building configuration...
Cryptochecksum: 35f32de6 81c535ed 3dce03ec 13f334ff
2568 bytes copied in 0.40 secs
[OK]
esxi1-asa2# reload
Proceed with reload? [confirm]
esxi1-asa2#
PostInstall configure:
1) Configure Split-tunnel for AnyConnect-Profile
Permit Any traffic (internet) when tunnel is UP.
Default: only protected traffic (10.1.1.0/24) is permited when tunnel comes UP.
group-policy GroupPolicy_ANYCONNECT-PROFILE attributes3) Permit Both profile selection: AnyConnect and Clientless Clients
wins-server none
dns-server value 8.8.8.8 8.8.4.4
vpn-tunnel-protocol ssl-client
split-tunnel-policy tunnelspecified
split-tunnel-network-list value MYLAN
...
access-list MYLAN line 1 remark MYLAN MGMT
access-list MYLAN line 2 standard permit 10.1.1.0 255.255.255.0
ASA 8.x: Allow Users to Select a Group at WebVPN Login via Group-Alias and Group-URL Method
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a00808bd83d.shtml
3) Enable Both: AnyConnect and Clientless Clients
Error: Clientless (browser) SSL VPN access is not allowed.
You can't have both AnyConnect Essential license and AnyConnect Premium license enabled at the same ASA. It is one or the other.
esxi1-ciscoasa-si(config)# webvpnhttps://supportforums.cisco.com/thread/2048458
esxi1-ciscoasa-si(config-webvpn)# no anyconnect-essentials